Natalie M. Scala
Associate Professor & Graduate Program Director, Towson University
Josh Dehlinger
Professor, Towson University
Yeabsira Mezgebe
Research Assistant & Graduate Student, Towson University
Much attention has been paid to cyber, physical, and
insider threats to an organization’s data and security.
Farahani, et al. (2016) in the Baltimore Business Review
identify major cyber breaches of companies and organizations
such as JP Morgan Chase, CareFirst Blue Cross
Blue Shield, eBay, and Home Depot, and propose best
practices to manage cyber risk. Since that article, insiders
with malicious intent have received widespread attention,
including major U.S. Government breaches driven
by Chelsea Manning and Edward Snowden. Insider
threats are related to human behavior and can range
from simple mistakes made by system users to deliberate,
malicious actions. A vast majority of insiders are
altruistic and do not intend harm but may introduce
risk through their mistakes or poor security behaviors.
Traditionally, the approach to managing organizational
insiders—defined by the U.S. Cybersecurity and Infrastructure
Security Agency as anyone who has access to
an organization’s network systems, data, or premises and
also uses that access (CISA, 2021)—has been monitoring,
surveillance, or other forms of supervision of the insiders’
interactions and use of cyber systems. However, a
new trend is emerging, where insider threats, which are
considered a problem driven by users, shifts to a framing
in terms of risk, which is instead driven by data (ARLIS,
2021). Considering insiders as threats is reactive, focusing
on the protection and privacy of an organization’s
data, and is structured around activities such as securing
email, web monitoring, and phishing attacks. However,
considering an organization’s insiders as potential risks,
but not necessarily threats, acknowledges the fact that
a vast majority of insiders are altruistic, shifting the
organization’s thinking to proactive by focusing on prevention
by means of a centralized policy or process. In
proactive insider risk management, the goal is to prevent
data leaks and breaches before they occur, rather than
reacting to what may have already happened.
The two approaches to insiders align with competing
definitions of metrics. In cybersecurity, metrics
are defined as best practices or predictive measures
to manage or mitigate threat; however, in analytics,
metrics are descriptive and focus only on the past and
present (Scala and Goethals, 2020). These definitions
generally align with the proactive/reactive approaches
to managing insiders. The key is to consider the level
of risk that an organization is willing to undertake as
well as the amount they can bear. Levels of risk may
not be consistent across organizations and may vary
by the type/size of firm, operating environment, cyber
maturity, nature or type of data to protect, etc. (Scala
and Goethals, 2020; Black, et al., 2018). Corresponding
metrics to define these polices are tough to develop but
are of great interest in the cybersecurity community.
Behavior Intent as Metrics
Assessing insider behavior intent is one method of defining
a metric for insider risk. The Security Behavior
Intentions Scale (SeBIS), developed by Egelman and
Peer (2015), is a validated inventory (Egelman, Harbach,
and Peer, 2016) that is accepted by the usable security
community to create characterizations based on
the respondents’ level of cyber and computer security
knowledge and savvy. Questions in the SeBIS inventory
focus on attitudes toward choosing passwords, securing
devices, updating protocols, and proactive awareness
(Egelman and Peer, 2015). Participants answer 16 questions
on a five-point Likert scale. The SeBIS inventory
measures participant intentions related to security and
how those intentions may vary between individuals; it
does not measure or predict actual behavior. However,
organizations can interdict on employee intentions with
the goal of poor approaches to security not becoming
actions. The outcomes and actions taken after a SeBIS
assessment of the workforce can empower insiders
to become part of a security solution and not another
source of risk.
Case Study: U.S. Elections Poll Workers
To illustrate the SeBIS inventory, consider poll workers
in U.S. elections. Poll workers are part of the first line of
defense in elections security; as such, they need to be
aware of and vigilant to real-time issues that may occur
and threats that may evolve on Election Day (Scala, et
al., 2020). As elections are primarily one-day events in
the U.S., they cannot be repeated or postponed. Consequently,
the security and integrity of the votes must be
maintained throughout the entire process. Poll workers
need knowledge of voting threats to be empowered to
mitigate and manage issues that may arise. However,
across the U.S., poll workers do not necessarily receive
threat training as part of election preparations.
Poll workers are trusted insiders to the voting process.
They have access to voting systems, which the Department
of Homeland Security classifies as critical infrastructure
(DHS, 2020). This includes paper ballots, electronic
voting cards, and all equipment used to administer an
election. In Maryland, this includes optical scanning
machines, electronic poll books, ballot marking devices,
and provisional voting materials. Furthermore, poll
workers are generally unsupervised while interacting
with equipment and related ballots. Thousands of poll
workers staff an election; Anne Arundel County alone
had over 1,900 poll workers for the 2020 November
General Election (Deville, 2020).
To deploy the SeBIS assessment, a data collection
campaign from June through November 2020 targeted
previous poll workers and/or those with intent to serve in
the 2020 U.S. General Election and yielded 2,213 viable
survey responses from 13 states. The target population
was recruited via email campaigns, social media, and
a postcard mailing; lists of poll workers for the email
campaign and postcard mailing were obtained from
county boards of elections and public records requests.
To our knowledge, this is the largest set of collected
SeBIS data responses of any population. Respondents
were presented the SeBIS survey from Egelman and Peer
(2015) in its entirety. Respondents were also screened to
ensure they previously served as a poll worker or had
intent to serve during the 2020 elections.
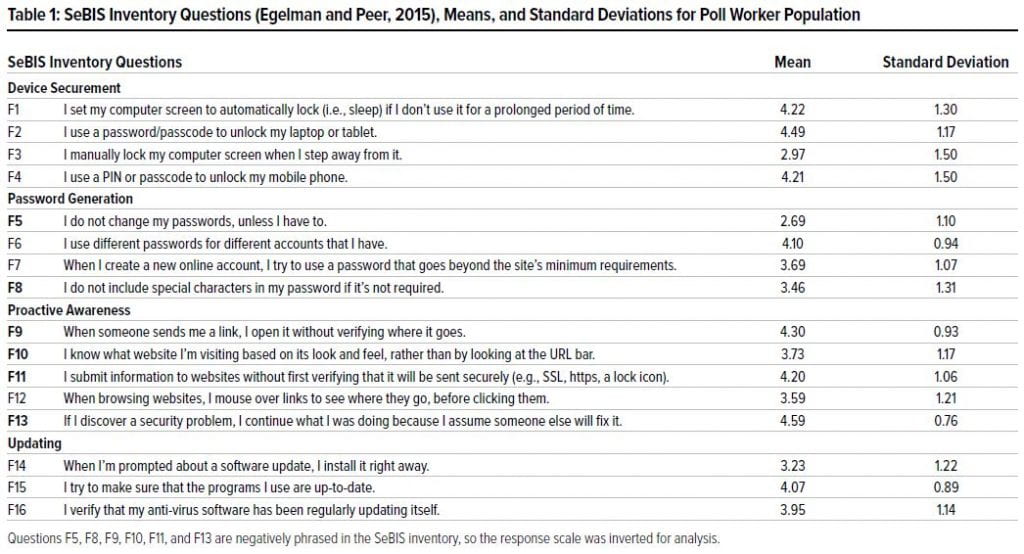
Table 1 presents the mean and standard deviation for
each SeBIS question response amongst all respondents;
the questions are numbered as they appear in the full
original inventory. Note that SeBIS is scored on a 1-5
Likert Scale, with responses ranging from never (1)
to always (5). Table 1 reflects that many poll workers
reported positive security intentions with their own
personal computing devices. Questions F5, F8, F9,
F10, F11, and F13 are negatively phrased in the SeBIS
inventory, so the response scale was inverted for analysis;
these questions are denoted in bold in Table 1. A
higher mean in Table 1 (closer to 5.00) implies stronger
security behavior intentions amongst the respondents.
It is also important to note that the standard deviations
in Table 1 imply the existence of variability in security
intentions amongst the respondents.
To further investigate the data, a Spearman rank-order
correlation analysis was performed on the entire data
set. Spearman’s rank-order correlation was used to
measure the strength and direction of the association
between respondents’ security intentions. Spearman
rank-order correlation analysis assumes that participants
were randomly selected; the selection of rank
is independent; and the relationship of one rank with
another is monotonic, which is appropriate for this
dataset (Kraska-Miller, 2013).
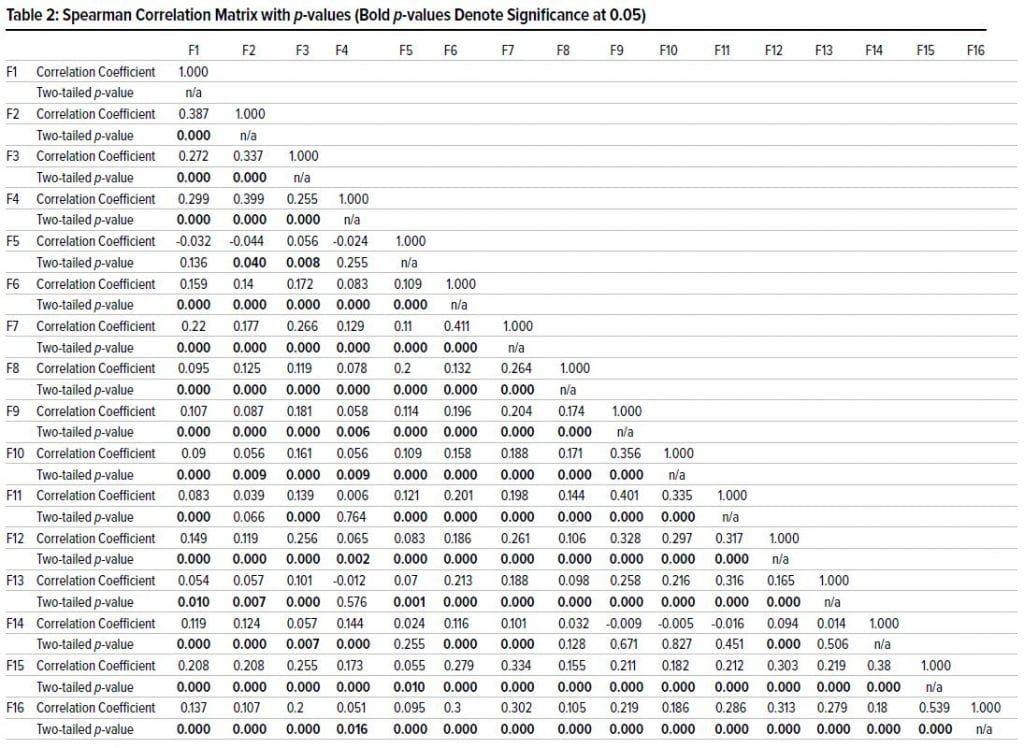
Table 2 presents the Spearman rank-order correlation
and corresponding p-values for the SeBIS inventory
questions. A significant positive correlation implies
that security intent either tends to increase or decrease
in parallel between the pairwise survey questions or
intentions being compared. A significant negative correlation
implies that security intentions tend to move in
opposite directions (i.e., one increases and one decreases)
between the pairwise survey questions.
Implementing Behavior Intent Metrics
A correlation analysis alone does not identify actions to
take or behavior intentions to consider for improving
polling place security and reducing poll worker insider
risk. However, to implement the insights from the correlation
analysis, organizations should partner with
their insiders and have them buy into becoming part of
proactive mitigation solutions. Poll workers are generally
altruistic insiders who are committed to their service;
therefore, empowering them with the means to identify
and mitigate risks and threats that may arise is critical.
This includes building positive feedback loops into
organizational culture that reward, instead of intimidate,
for participation in the organization’s security posture.
Training is also a key component; Scala, et al. (2020)
propose online learning modules for poll workers to
identify and mitigate potential threats that may arise at a
polling place. That training, which was utilized in Anne
Arundel County during the 2020 General Election (Deville,
2020), and statistically significantly increased poll worker
threat awareness (Scala, et al., 2020), can be extended
to include targeted correlated behavior intentions from
the SeBIS inventory. Such improvements will create
more robust insider risk training, directly addressing
potential shortcomings in particular security intentions.
Finally, security workarounds that employees may be
using should be identified and mitigated by designing
policies that support work efficiencies but also strong
security-minded behaviors.
Even though this case study examined poll worker
behavior intentions, the same approach can be applied
when considering the cyber, physical, and insider security
of supply chains. For example, if the organization is
worried about data breaches, it can deploy the inventory
and use highly-correlated SeBIS intentions to understand
current employees’ behavior intentions, followed by
developing and/or adjusting policies, practices, and
training accordingly to help prevent a breach.
An organization can also use SeBIS to gain insight on
its data locality, data visibility, fraud prevention, and
third-party risk. A related example is the March 2021
SolarWinds data breach. In early 2020, hackers secretly
broke into SolarWinds and added malicious code to the
software system (Jibilian, 2021). SolarWinds unwittingly
sent out software updates to its customers that had the
malicious codes, which created a backdoor to customers’
IT systems. Then the hackers installed even more
malicious codes that helped them spy on companies
and organizations.
The need for organizations to develop a proactive security
posture to protect the integrity of sensitive data
and processes is essential to maintain public trust and
organizational viability. Yet, many organizations focus
solely on developing risk assessments and mitigations
to protect from external actors; an organization intent
on developing a strong security posture needs to additionally
understand, assess, and train for risks that may
arise from insiders.
References
ARLIS: Applied Research Laboratory for Intelligence and Security.
(2021, March 30). IRISS event summary #1: State of insider threat and
insider risk paradigms. https://arlis8.umd.edu/iriss-event-summary-
1-state-insider-threat-and-insider-risk-paradigms-1
Black, L., Scala, N. M., Goethals, P. L., & Howard II, J. P. (2018). Values
and trends in cybersecurity. Proceedings of the 2018 Industrial and
Systems Engineering Research Conference. https://tinyurl.com/Black-
EtAl2018
Cybersecurity and Infrastructure Security Agency. (2021, September
28). Insider threat mitigation. https://www.cisa.gov/insider-threatmitigation
Department of Homeland Security. (2020, July 14). Election security.
https://www.dhs.gov/topic/election-security
Deville, T. (2020, October 16). Towson University professor aims
to bolster local election security at voting sites. The Baltimore
Sun. https://www.baltimoresun.com/maryland/baltimore-county/
cng-co-ca-at-towson-election-security-20201016-vrovdo7qyvdu7h2nmyk7addbli-
story.html
Egelman, S., Harbach, M., & Peer, E. (2016). Behavior ever follows
intention? A validation of the Security Behavior Intentions Scale
(SeBIS). Proceedings of the 2016 CHI Conference on Human Factors in
Computing Systems, 5257-5261.
Egelman, S. & Peer, E. (2015). Scaling the security wall: Developing a
Security Behavior Intentions Scale (SeBIS). Proceedings of the 33rd
Annual ACM Conference on Human Factors in Computing Systems,
2873-2882.
Farahani, J., Scala, N. M., Goethals, P., & Tagert, A. (2016). Best
practices in cybersecurity: Processes and metrics. Baltimore Business
Review: A Maryland Journal, 28-32.
Jibilian, I. (2021, April 15). The US is readying sanctions against Russia
over the SolarWinds cyber-attack. Here’s a simple explanation of how
the massive hack happened and why it’s such a big deal. Business
Insider. https://www.businessinsider.com/solarwinds-hack-explainedgovernment-
agencies-cyber-security-2020-12.
Kraska-Miller, M. (2013). Nonparametric statistics for social and behavioural
sciences. Boca Raton: CRC Press.
Scala, N. M., Dehlinger, J., Black, L., Harrison, S., Delgado Licona, K.,
& Ieromonahos, A. (2020). Empowering election judges to secure our
elections. Baltimore Business Review: A Maryland Journal, 8-20.
Scala, N. M. & Goethals, P. L. (2020). A model for and inventory of
cybersecurity values: Metrics and best practices. In N. M. Scala and
J. P. Howard II (Eds.), Handbook of Military and Defense Operations
Research (pp. 305-330). CRC Press.