Megan Price
Business Administration Graduate of Towson University
Natalie M. Scala, Ph.D.
Assistant Professor and Graduate Program Director at Towson University
COL Paul L. Goethals, Ph.D.
Academy Professor at the United States Military Academy
The Help America Vote Act of 2002 made sweeping reforms to the nation’s voting processes to include replacing electronic voting equipment and phasing out paper punch cards, the latter of which became a point of contention during the 2000 Presidential election (US EAC, 2018). The integrity of the new electronic systems was not challenged until the 2016 Presidential election, when the Department of Homeland Security admitted that the voting systems from 21 states, including Maryland, were targets of attacks (Horwitz, Nakashima, and Gold, 2017). Such news, along with continued mainstream media reporting regarding interference by and continued potential for a foreign actor or nation state to influence or destabilize the outcome of an election, has led to concern about the integrity of voting processes (NYT, 2018).
Our applied research addresses these concerns and explicitly speaks to the security of Maryland’s voting processes by developing process maps for election systems, identifying vulnerabilities in the voting process based upon these process maps, and establishing a risk model framework to assess and mitigate the vulnerabilities. We also contribute public service education of training modules for Election Judges, providing guidelines and best practices for poll workers to identify and mitigate threats, which supports the overall security of the voting systems. We partner with Harford County, Maryland, to identify specific cyber, physical, and human vulnerabilities in the election process. The State of Maryland uses the same election process throughout the state, so by analyzing Harford County’s election process, we generalize our results to the overall process for Maryland. Our methodology can also be extended to industries at large, as a basic approach for identifying and mitigating potential cyber vulnerabilities.
The Center for American Progress (Root, et al., 2018a) conducted a detailed study of each state’s election systems, along with the District of Columbia, and created a grade for each state based on the requirements and practices related to audit trails, absentee ballots, voting machines, and voter registration systems. Grades ranged from A to F, similar to a report card. Maryland was a top scoring state with an overall grade of B, implying that the state is rather secure in its voting process. No state received a grade of A (Root, et al., 2018b). According to the report, Maryland adheres to cybersecurity standards and has a paper audit trail, but struggles with post-election audits. Therefore, opportunities for improving the voting process exist; in general, states must be responsive to evolving and adaptive adversaries.
Risk Model
Risks and threats to voting systems can be organized into three groups: cyber, physical, and insider. Cyber-related threats include the use of digital machines and media for collecting, tallying, and transmitting votes, regardless of any existence of an Internet connection in the system. Physical threats involve tampering with equipment before, during, or after Election Day. Human behavior threats are related to adversary or insider actions, which can range from simple mistakes made by users to a malicious actor’s deliberate actions of ill-harm to a system or the process. To facilitate an understanding of the total risk in the Maryland elections process, we examined the literature on voting vulnerabilities (e.g. Blaze, et al., 2017; Brunner, 2007; Cahn, 2017), reviewed Election Judge training manuals (Keene and Livingston, 2016), toured a mock precinct polling place, and interviewed officials at the Harford County Board of Elections. Gathering data at large from the literature as well as details specific to the Harford County process helped to assess the relative security of the elections equipment as well as holistically determine any and all vulnerabilities in the current process.
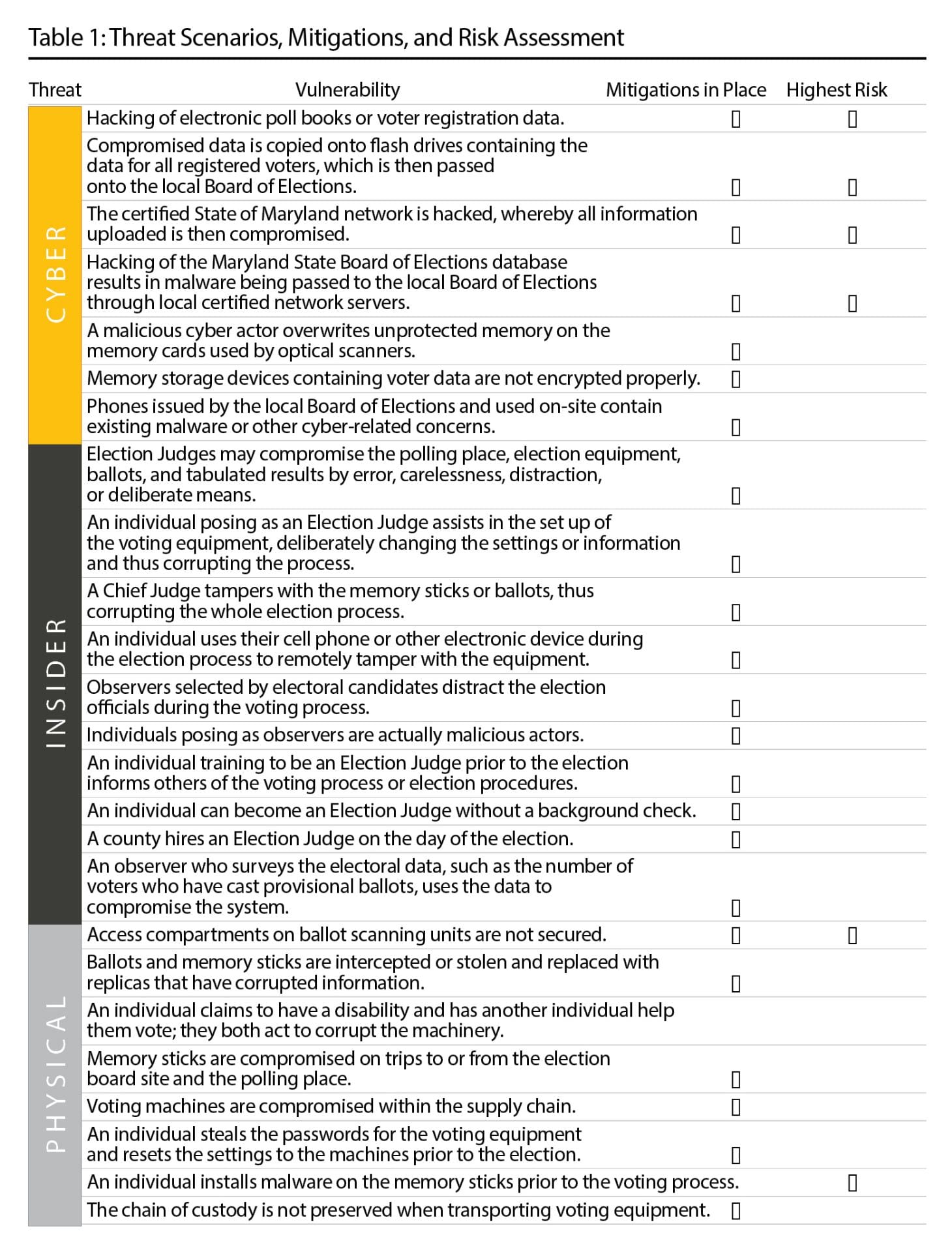
Our analysis identified 25 vulnerabilities in the Harford County process as of the 2018 primary election, which are outlined in Table 1. Note that concerns span cyber, physical, and insider threats, and these vulnerabilities are a list of potential ways the process can be impacted. We have no data to support that the process has already been impacted negatively in these ways. Figure 1 provides an illustration of the elections process, mapping out the events from when the voter checks into the polling facility to when their ballot is cast. Responsibilities and decisions for both the election official and voter are also shown to aid in identifying who is responsible for each task and making decisions. Understanding roles of voting process administrators and how they relate to the process facilitates an overall awareness of the potential actions that can mitigate threats.
Figure 1: Voting Process Map
The State of Maryland and Harford County are already mitigating some of these vulnerabilities through various initiatives and policies. However, in order to understand if enough action is being taken along with the extent of the risk associated with each vulnerability, we develop a model to assess total risk and identify various focus areas for mitigating weaknesses. Through an exhaustive literature search, interviews with Board of Elections personnel, multiple site visits, and a review of best practices in cybersecurity, we identify potential mitigations to decrease the probability and impact of an attack. These mitigations include some practices already in place and other suggestions that we develop. Table 1 identifies the vulnerabilities that have current mitigations in place. For example, mitigating weak passwords includes changing passwords for every election, securing the passwords before and after use, and updating passwords from equipment defaults. Weak encryption can be improved by changing the default encryption settings and wiping the data from each memory card after each use. Vulnerabilities associated with memory can be mitigated by using strong encryption, changing the memory cards for each election, wiping the data off of the memory card after use, building memory cards to detect changes in software, and keeping the cards locked with unique keys and limited access.
Malware concerns can be mitigated by the state informing localities of potential attacks, building equipment to detect changes in software, auditing the equipment before use with a paper trail, and providing limited access to the equipment. A break in the chain of custody for equipment can be mitigated by ensuring bipartisan teams watch the memory sticks at all times, restricting access to equipment while not in use, building equipment to detect changes in software, and auditing equipment upon arrival at each destination.
The first phase of the risk model is a proof of concept to identify the vulnerabilities considered most risky, specifically those that warrant the greatest attention from the state. To fully understand threat, we employ data from the United States Elections Assistance Commission (2009), which are a comprehensive inventory of attack trees for various types of elections equipment, including the precinct count optical scanning devices used in Maryland. This analysis led to a score related to the probability of an attack against a vulnerability occurring. The score, which is developed by our team, relates to the frequency of T (terminal), A (and), and O (or) nodes on the attack tree and its association with a given vulnerability. Then, vulnerabilities earning scores above a certain threshold score are identified as the riskiest and therefore require the most attention when mitigating threats. Table 1 identifies which cyber, physical, and insider vulnerabilities fall into this category.
The next step is to extend the risk model to a Markov Chain representation, in order to holistically examine tradeoffs between cyber, physical, and insider threats. Such a model will further develop the probability assessment for every vulnerability and also identify when an attack is most likely to occur in the elections process (election preparation, in-person voting, and wrap-up voting). These extensions will demonstrate an evolving threat posture over time and can generalize the model beyond Maryland’s process.
Election Judge Training
Identifying vulnerabilities are of concern, but Election Judges need to be empowered to respond to and mitigate cyber, physical, and insider threats if they occur at a polling place. The second phase of our research develops training modules for Election Judges. Currently, poll workers in Maryland do not receive training in cybersecurity awareness. All training is done in person and can begin a few months before the election. We are developing short 20-minute online modules that Election Judges can view and interact with to gain cyber awareness and threat training. These modules will be used by Harford County as a refresher for judges before Election Day and will be administered via the Cyber4All initiative, which is run by the Department of Computer and Information Sciences at Towson University. This phase of our research translates the academic risk model into action and enables Election Judges to become the first line of defense to the integrity of votes cast on an Election Day.
Extensions
The approach offered in this research can be extended beyond voting processes. Firms can use this methodology to identify potential cyber, physical, and insider threats in their own organizational systems. Then, risk models can be formulated to identify the most important vulnerabilities to mitigate, coupled with employee training, to respond to threats. Such an approach extends cybersecurity concerns into a holistic assessment of the entire system, examining tradeoffs and identifying where to focus critical resources and budget expenditures.
Conclusions
Threats to the country’s voting systems are persistent and evolving. Most academic research examining threats to the voting process focus on the state’s role. In contrast, this research examines threat at the local precinct level, where the public actually interacts with the voting process. In doing so, the findings may be more practical for election officials to implement in voting processes. Our partnership with Harford County leads to applied impact to increase the integrity of votes cast on Election Day. While Maryland has one of the most secure voting processes, room for improvement exists. By addressing weaknesses found in our state’s voting systems, Towson University continues to take a leading role in community engagement, improving security for the citizens of Maryland.
Disclaimer
The views expressed in this paper are those of the authors, and do not represent the official policy or position of the United States Military Academy, the United States Army, or the United States Department of Defense.
References
- Blaze, M., Braun, J., Hursti, H., Hall, J. L., MacAlpine, M., & Moss, J. (2017). DEFCON 25 Voting Machine Hacking Village. Proceedings of DEFCON, Washington D.C. 1-18.
- Brunner, J. (2007). Hart System. (Report No. 1). Ohio: Microsolved, Inc.
- Cahn, D. (2017). Risk Assessment: How Secure are Voting Machines (Unpublished thesis) University of Pennsylvania, Philadelphia, PA.
- Horwitz, S., Nakashima, E., & Gold, M. (2017). DHS tells states about Russian hacking in 2016 election. The Washington Post
- https://tinyurl.com/HorwitzEtAlKeene, K. K. & Livingston, D. E. (2016). Election Judge Manual 2016. Forest Hill, Maryland: Harford County Board of Elections.
- The New York Times (2018). Russian hacking and influence in the U.S. election. Retrieved from https://www.nytimes.com/news-event/russian-election-hacking
- Root, D., Kennedy, L., Sozan, M., & Parshall, J. (2018a). Election security in all 50 states. Retrieved from
- https://www.americanprogress.org/issues/democracy/reports/2018/02/12/446336/election-security-50-states/
- Root, D., Kennedy, L., Sozan, M., & Parshall, J. (2018b). Election security in all 50 states: Defending America’s elections. Retrieved from
- https://cdn.americanprogress.org/content/uploads/2018/02/21105338/020118_ElectionSecurity-report11.pdf#page=31
- United States Election Assistance Commission Advisory Board & United States Election Assistance Commission Standards Board (2009). Election operations assessment: Threat trees and matrices and threat instance risk analyzer (TIRA). Retrieved from
- https://www.eac.gov/assets/1/28/Election_Operations_Assessment_Threat_Trees_and_Matrices_and_Threat_Instance_Risk_Analyzer_(TIRA).pdf
- United States Election Assistance Commission (2018). Help America Vote Act. Retrieved from https://www.eac.gov/about/help-america-vote-act/